Home>Software and Apps>Enhancing Online Security with Talkatone VPN

Software and Apps
Enhancing Online Security with Talkatone VPN
Modified: September 5, 2024
Protect your online activities with Talkatone VPN. Secure your data and privacy while using software and apps. Enhance your online security today!
(Many of the links in this article redirect to a specific reviewed product. Your purchase of these products through affiliate links helps to generate commission for Techsplurge.com, at no extra cost. Learn more)
Table of Contents
Enhancing Online Security with Talkatone VPN
In today's digital age, online security is more crucial than ever. With the rise of remote work, online shopping, and social media usage, individuals are increasingly exposed to cyber threats. One effective way to enhance online security is by using a Virtual Private Network (VPN). This article explores the concept of VPNs, the importance of using one, and how Talkatone VPN can specifically help in securing your online activities.
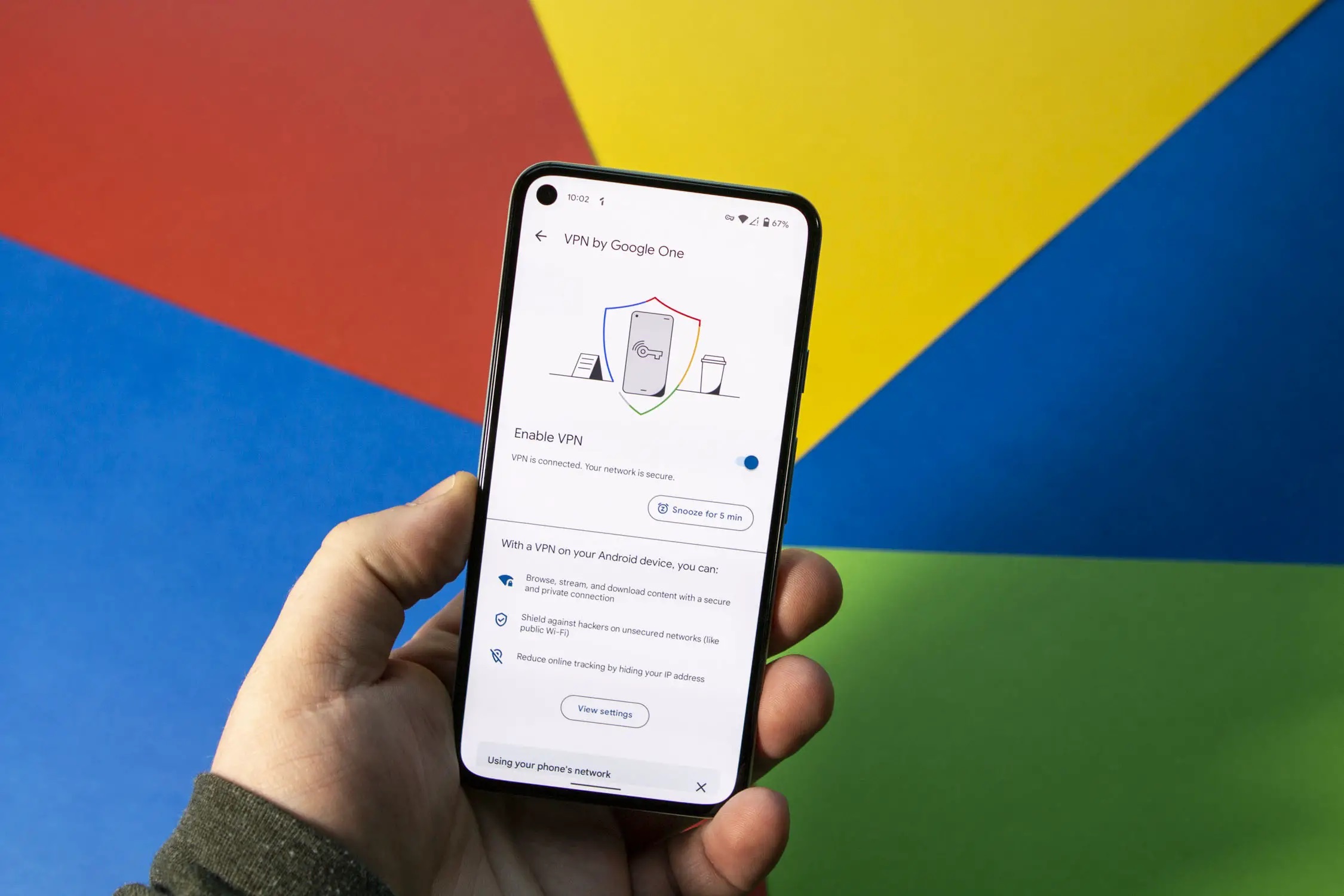
What is a VPN?
A VPN is a service that creates a secure, encrypted connection over the internet between your device and a VPN server. This connection masks your IP address, making it difficult for hackers and third parties to track your online activities. VPNs are commonly used by individuals who want to protect their data while using public Wi-Fi networks, accessing geo-restricted content, or simply ensuring their online privacy.
How Does a VPN Work?
Here’s a step-by-step explanation of how a VPN works:
- Connection Establishment: When you connect to a VPN, your device establishes a secure connection with the VPN server. This connection is typically encrypted using protocols like OpenVPN, L2TP/IPSec, or PPTP.
- IP Address Masking: Once connected, your device’s IP address is masked by the VPN server’s IP address. This makes it appear as though you are accessing the internet from the VPN server’s location rather than your actual location.
- Data Encryption: All data transmitted between your device and the VPN server is encrypted. This ensures that even if someone intercepts your data, they won’t be able to read it without the decryption key.
- Secure Browsing: With your IP address masked and data encrypted, you can browse the internet securely. This is particularly important when using public Wi-Fi networks, which are often vulnerable to hacking.
Importance of Using a VPN
Using a VPN is essential for several reasons:
Protection Against Hackers
Public Wi-Fi networks are notorious for being insecure. Hackers often target these networks to steal sensitive information like passwords, credit card details, and personal data. A VPN encrypts your data, making it difficult for hackers to intercept and misuse your information.
Read more: Enhancing Online Security with NordVPN
Geo-Restrictions
Many websites and services are geo-restricted, meaning they can only be accessed from specific locations. A VPN allows you to bypass these restrictions by masking your IP address and making it appear as though you are accessing the internet from a different location.
Online Privacy
In today’s digital age, online privacy is a significant concern. Governments and corporations often collect user data without consent. A VPN helps protect your online activities by masking your IP address and encrypting your data, making it difficult for third parties to track your activities.
Secure Remote Work
With the rise of remote work, employees often access company resources from public Wi-Fi networks or personal devices. A VPN ensures that all data transmitted between the employee’s device and the company’s servers is encrypted and secure.
Talkatone VPN: A Comprehensive Review
Talkatone VPN is a robust VPN service designed to enhance online security and privacy. Here’s a detailed review of its features and benefits:
Security Features
Talkatone VPN uses advanced encryption protocols to ensure that all data transmitted between your device and the VPN server is secure. It supports multiple protocols including OpenVPN, L2TP/IPSec, and PPTP, providing users with flexibility in choosing the best protocol for their needs.
Server Locations
Talkatone VPN has a vast network of servers located in various parts of the world. This allows users to choose servers based on their location, ensuring faster speeds and better connectivity.
Speed and Performance
One of the key concerns with VPNs is speed. Talkatone VPN has optimized its servers to provide fast speeds without compromising on security. Users can enjoy seamless browsing and streaming experiences even when connected to the VPN.
User-Friendly Interface
Talkatone VPN offers a user-friendly interface that makes it easy for anyone to set up and use. The app is available for both desktop and mobile devices, ensuring that users can stay secure on the go.
Customer Support
Talkatone VPN provides excellent customer support. Users can reach out to the support team via email or live chat for any queries or issues they may face. The support team is responsive and knowledgeable, ensuring that users get the help they need quickly.
Privacy Policy
Talkatone VPN has a strict no-logs policy, meaning it does not store any user data. This ensures that users’ online activities remain private and secure.
How to Use Talkatone VPN
Using Talkatone VPN is straightforward. Here’s a step-by-step guide on how to set it up:
- Download and Install the App: Download the Talkatone VPN app from the official website or app store. Install it on your device.
- Sign Up: Create an account on the Talkatone VPN website. You will need to provide some basic information such as your email address and password.
- Choose a Plan: Talkatone VPN offers various plans to suit different needs. Choose a plan that best fits your requirements.
- Connect to a Server: Launch the app and connect to a server of your choice. You can select servers based on location or speed.
- Verify Connection: Once connected, verify that your IP address has been masked by checking a website like whatismyip.com.
- Enjoy Secure Browsing: With your connection established, you can now browse the internet securely using Talkatone VPN.
Enhancing online security is crucial in today’s digital world. Using a VPN like Talkatone is an effective way to protect your data from hackers, bypass geo-restrictions, and maintain online privacy. With its robust security features, user-friendly interface, and excellent customer support, Talkatone VPN is an excellent choice for anyone looking to enhance their online security.
While there are many VPN services available, Talkatone VPN stands out due to its comprehensive features and commitment to user privacy. By using Talkatone VPN, you can enjoy secure browsing and peace of mind knowing that your online activities are protected.