Home>Software and Apps>Exploring Amazon’s PV VPN: A Tech Blog Review

Software and Apps
Exploring Amazon’s PV VPN: A Tech Blog Review
Modified: September 5, 2024
Discover the latest insights on Amazon's PV VPN and other software and apps in this comprehensive tech blog review. Explore expert opinions and recommendations.
(Many of the links in this article redirect to a specific reviewed product. Your purchase of these products through affiliate links helps to generate commission for Techsplurge.com, at no extra cost. Learn more)
Table of Contents
Introduction
In cybersecurity and digital privacy, Amazon has introduced a new feature: Amazon's Personal VPN. This service promises to enhance user security and anonymity by encrypting internet traffic. It is a compelling option for both personal and professional use. This article will cover Amazon's Personal VPN, exploring its features, benefits, and potential drawbacks. A comparison with other VPN services will also be provided.
What is Amazon's Personal VPN?
Amazon's Personal VPN is a virtual private network service designed to provide users with an additional layer of security and privacy when browsing the internet. Unlike traditional VPNs that often require users to download and install software or apps, Amazon's Personal VPN is integrated directly into the Amazon ecosystem. This means that users can easily activate and manage their VPN settings through their Amazon account, making it a seamless and user-friendly experience.
Key Features
- Ease of Use: One of the standout features of Amazon's Personal VPN is its simplicity. Users can activate the VPN with just a few clicks, making it accessible to those who may not be tech-savvy.
- Integration with Amazon Services: Since it is part of the Amazon ecosystem, the VPN integrates well with other Amazon services like Prime Video and Amazon Music. This integration ensures that users can enjoy secure streaming without any hassle.
- Security: The VPN uses robust encryption protocols to protect user data. This ensures that even if a user is connected to a public Wi-Fi network, their internet traffic remains encrypted and secure.
- Speed: Amazon's Personal VPN is designed to minimize speed loss, ensuring that users can enjoy fast and reliable internet speeds even when the VPN is active.
- Multi-Device Support: The service supports multiple devices, including smartphones, tablets, smart TVs, and even smart home devices. This makes it an excellent choice for households with multiple devices.
Benefits of Using Amazon's Personal VPN
- Enhanced Security: The primary benefit of using Amazon's Personal VPN is enhanced security. By encrypting internet traffic, the VPN protects users from cyber threats such as hacking, eavesdropping, and data breaches.
- Anonymity: The VPN helps users maintain anonymity online by masking their IP addresses. This is particularly useful for those who want to browse the internet without being tracked by advertisers or governments.
- Protection Against Public Wi-Fi Threats: Public Wi-Fi networks are often vulnerable to cyber attacks. Amazon's Personal VPN provides a secure connection even when users are connected to public Wi-Fi networks, protecting them from potential threats.
- Compliance with Data Privacy Regulations: In an era where data privacy regulations like GDPR and CCPA are becoming increasingly stringent, Amazon's Personal VPN helps users comply with these regulations by ensuring that their data is protected.
- Peace of Mind: For users who are concerned about their online security, Amazon's Personal VPN offers peace of mind. Knowing that their internet traffic is encrypted and secure can reduce stress and anxiety associated with online activities.
Potential Drawbacks
- Limited Customization Options: Unlike some other VPN services, Amazon's Personal VPN does not offer extensive customization options. Users cannot choose specific servers or protocols, which might be a drawback for advanced users.
- Dependence on Amazon Services: Since the VPN is integrated into the Amazon ecosystem, users must have an active Amazon account to use it. This dependence on Amazon services might be a concern for those who prefer to use standalone VPN solutions.
- Cost: While Amazon's Personal VPN is included with some Amazon services, it may not be available as a standalone service. This could make it more expensive than other VPN options available in the market.
- Performance Issues: Some users might experience performance issues, such as slower speeds or dropped connections, although Amazon has optimized the service to minimize these problems.
Comparison with Other VPN Services
Amazon's Personal VPN is not the only VPN service available in the market. Here’s a brief comparison with some popular VPN services:
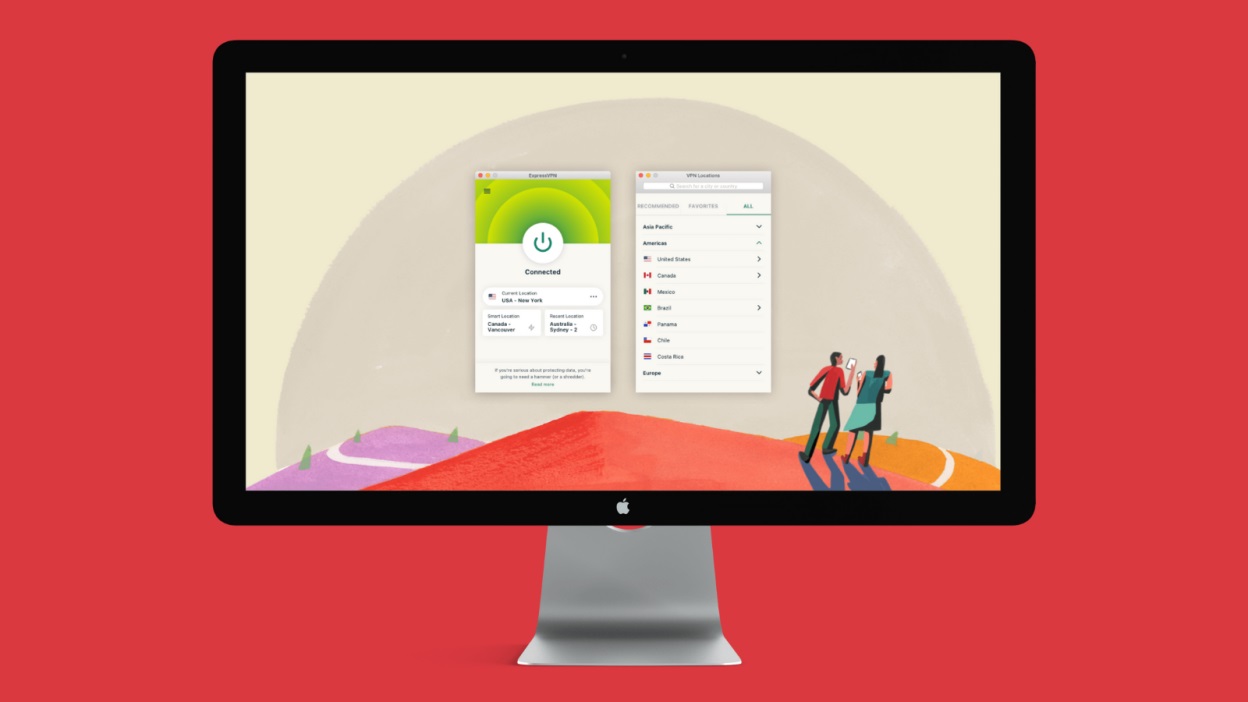
ExpressVPN
- Customization Options: ExpressVPN offers extensive customization options, including the ability to choose specific servers and protocols.
- Speed: ExpressVPN is known for its fast speeds, making it ideal for streaming and online gaming.
- Price: ExpressVPN is generally more expensive than Amazon's Personal VPN, especially if users opt for the premium features.
NordVPN
- Security Features: NordVPN is renowned for its robust security features, including double encryption and a no-logs policy.
- Server Network: NordVPN has an extensive server network, providing users with a wide range of options.
- Price: NordVPN is competitive in terms of pricing, offering both basic and premium plans.
ProtonVPN
- Free Version: ProtonVPN offers a free version with limited features, making it an excellent option for those on a budget.
- Security Focus: ProtonVPN is highly focused on security, using advanced encryption protocols and a no-logs policy.
- Price: ProtonVPN is generally more affordable than Amazon's Personal VPN, especially for those who opt for the free version.
Read more: Tech Blog: Exploring the World of Subtitles
Final Thoughts
Amazon's Personal VPN is a robust and user-friendly solution for enhancing online security and anonymity. While it may have some limitations in terms of customization options and cost, it offers a seamless integration with Amazon services and robust encryption protocols. For users who are already part of the Amazon ecosystem, this VPN can be a valuable addition to their digital security arsenal. However, for those who prefer standalone VPN solutions or need more advanced features, other options like ExpressVPN, NordVPN, and ProtonVPN might be more suitable.