Home>Software and Apps>Exploring the World of Windows VPN: Unveiling the Power of Virtual Private Networks


Software and Apps
Exploring the World of Windows VPN: Unveiling the Power of Virtual Private Networks
Modified: September 5, 2024
Discover the best Windows VPN software and apps for secure and private browsing. Explore the power of virtual private networks and enhance your online experience. Unlock a world of possibilities with VPN technology.
(Many of the links in this article redirect to a specific reviewed product. Your purchase of these products through affiliate links helps to generate commission for Techsplurge.com, at no extra cost. Learn more)
Table of Contents
What is a VPN?
A VPN, or Virtual Private Network, creates a secure, encrypted online connection between your device and a VPN server. This connection extends a private network across a public one, allowing users to send and receive data securely and privately.
How VPNs Work
When connected to a VPN, data is encapsulated in a tunneling protocol, encrypting it at the sending end and decrypting it at the receiving end. This encryption ensures that even if intercepted, the data remains indecipherable without the encryption keys. The VPN connection appears as a dedicated private link from your device to the VPN server, masking your IP address and location, thereby protecting online activities.
Components of a VPN
- VPN Client: The device or software application that initiates the VPN connection. It can be an individual computer or a router initiating a site-to-site connection.
- VPN Server: The server that listens for VPN connection attempts and responds to the request to create a connection. In site-to-site VPNs, the answering router acts as the VPN server.
- VPN Tunnel: The portion of the connection where data is encapsulated and encrypted. The tunnel ensures that data travels securely over the public internet.
- Tunneled Data: Data sent across the private point-to-point link created by the VPN tunnel.
Types of VPNs
- Remote Access VPN: Allows users to connect to a private network from a remote location, such as from home or while traveling. Commonly used by employees needing secure access to company resources from outside the office.
- Site-to-Site VPN: Connects multiple networks within an organization or between different organizations. Useful for large organizations with departments across multiple locations, ensuring secure communication and resource sharing.
- Mobile VPN: Designed for smartphone users, mobile VPNs provide the same level of security as traditional VPNs but also handle spotty or unstable internet connections. Essential for users needing protection while on the go.
Benefits of Using a VPN
- Enhanced Security: Encrypting data protects it from interception by third parties, including hackers and ISPs, ensuring sensitive information remains confidential.
- Privacy Protection: Masks your IP address and location, hiding browsing activity and identity. Prevents third-party tracking, ensuring online activities remain private.
- Access to Restricted Content: Bypasses geographical restrictions and content blocks, allowing access to content restricted in certain regions.
- Protection Against ISP Tracking: Prevents ISPs from monitoring online activities, ensuring data remains private.
- Secure File Sharing: Enables secure file sharing between different locations, crucial for businesses and organizations needing to share sensitive information.
Practical Applications of VPNs
- Business Use: Organizations use VPNs to ensure authorized users can access their data center using encrypted channels. Particularly important for remote workers needing secure access to company resources.
- Personal Use: Individuals use VPNs to protect personal data while using public Wi-Fi networks or when accessing sensitive information online. Useful for bypassing geo-restrictions on streaming services or social media platforms.
- Travelers: Travelers rely on VPNs to protect data while using public Wi-Fi networks in hotels, cafes, or airports. Ensures personal information remains secure even in unfamiliar environments.
- Online Gaming: Gamers use VPNs to reduce latency and improve gaming experiences by connecting to servers closer to their location. Additionally, VPNs help protect gamers from DDoS attacks and other online threats.
Setting Up a VPN on Windows
Setting up a VPN on Windows is straightforward and can be done using the built-in Windows VPN client or third-party VPN software.
Using the Built-in Windows VPN Client
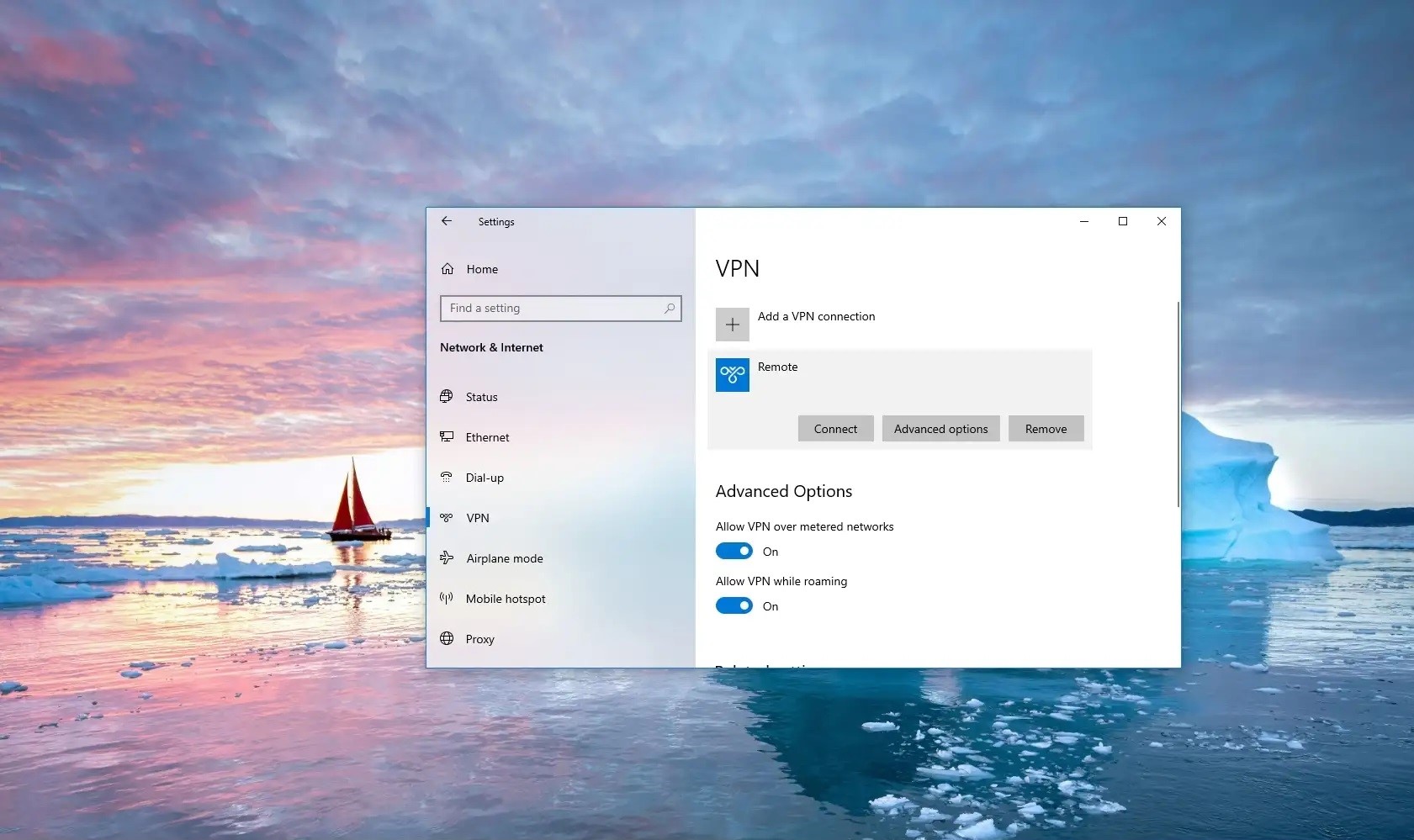
- Open Settings: Go to the Start menu and select "Settings."
- Network & Internet: Click on "Network & Internet."
- VPN: Click on "VPN."
- Add a VPN Connection: Click on "Add a VPN connection."
- Choose a VPN Provider: Select your VPN provider from the list of available options.
- Enter VPN Details: Enter the server address, username, and password provided by your VPN provider.
- Save the Connection: Click on "Save" to save the new VPN connection.
Using Third-Party VPN Software
- Download and Install VPN Software: Download and install third-party VPN software such as ExpressVPN, NordVPN, or TunnelBear.
- Launch the VPN Software: Launch the VPN software and sign in with your account credentials.
- Connect to a VPN Server: Select a VPN server from the list of available options and click on "Connect."
- Verify Connection: Once connected, verify that your IP address has changed and you are now using the VPN server's IP address.
Read more: Tech Blog: Exploring the World of Subtitles
Common VPN Protocols
VPNs use various tunneling protocols to establish secure connections. Some of the most common protocols include:
- PPTP (Point-to-Point Tunneling Protocol): Developed by Microsoft in 1996, PPTP is one of the oldest VPN protocols but is less secure compared to modern protocols.
- L2TP/IPSec (Layer 2 Tunneling Protocol/Internet Protocol Security): More secure than PPTP and widely used due to its robust encryption and authentication mechanisms.
- OpenVPN: An open-source protocol offering high security and flexibility. Widely used due to its customizability and strong encryption.
- SSTP (Secure Socket Tunneling Protocol): Developed by Microsoft, SSTP is a secure protocol using SSL/TLS encryption to secure data transmission.
Choosing the Right VPN
Choosing the right VPN involves considering several factors, including security, speed, server locations, and customer support.
- Security: Look for a VPN using strong encryption protocols such as AES-256 and supporting multiple protocols like OpenVPN, L2TP/IPSec, and SSTP.
- Speed: A fast VPN is essential for smooth browsing and streaming experiences. Look for VPNs offering high-speed servers and minimal latency.
- Server Locations: Ensure the VPN has servers in multiple locations around the world to provide access to geo-restricted content and better performance.
- Customer Support: Good customer support is crucial in case of any issues with the VPN. Look for VPNs with 24/7 customer support and a comprehensive knowledge base.