Home>Software and Apps>Exploring Windows VPN Port: A Comprehensive Guide

Software and Apps
Exploring Windows VPN Port: A Comprehensive Guide
Modified: September 5, 2024
Discover everything you need to know about Windows VPN port, including setup, troubleshooting, and best software and apps for a secure connection. Explore now!
(Many of the links in this article redirect to a specific reviewed product. Your purchase of these products through affiliate links helps to generate commission for Techsplurge.com, at no extra cost. Learn more)
Table of Contents
Introduction
Virtual Private Networks (VPNs) have become essential for securing internet connections, especially when accessing sensitive information over public networks. Windows, being one of the most widely used operating systems, provides robust support for VPNs, allowing users to create and manage VPN connections with ease. This article provides a comprehensive guide on setting up, managing, and troubleshooting VPN connections on Windows.
Understanding VPNs
Before diving into the specifics of setting up a VPN on Windows, it's crucial to understand what a VPN is and how it works. A VPN creates a secure, encrypted tunnel between your device and a VPN server, masking your IP address and encrypting your internet traffic. This ensures that your online activities remain private and secure, even when using public Wi-Fi networks.
Types of VPNs
There are several types of VPNs, each with its own set of features and uses:
- Remote Access VPNs: These allow remote users to connect to a company's network securely over the internet.
- Site-to-Site VPNs: These connect entire networks together, allowing secure communication between different sites.
- Client-to-Site VPNs: These connect a single client to a VPN server, often used for personal VPNs.
Setting Up a VPN on Windows
To set up a VPN on Windows, you need to create a VPN profile. Here’s a step-by-step guide:
Step 1: Create a VPN Profile
- Open Settings: Click on the Start button and select Settings.
- Network & Internet: Navigate to Network & Internet.
- VPN: Click on VPN.
- Add a VPN Connection: Click on Add a VPN connection.
Step 2: Choose the VPN Provider
- VPN Provider: Select Windows (built-in) as the VPN provider.
- Connection Name: Enter a name for your VPN connection (e.g., My Personal VPN).
- Server Name or Address: Enter the address of the VPN server you want to connect to.
- VPN Type: Choose the type of VPN connection you want to create (e.g., IKEv2, OpenVPN, L2TP/IPSec).
- Type of Sign-in Info: Choose the type of sign-in information required (e.g., username and password, one-time password, certificate).
Step 3: Save the VPN Profile
- Save: Click on Save to save the VPN profile.
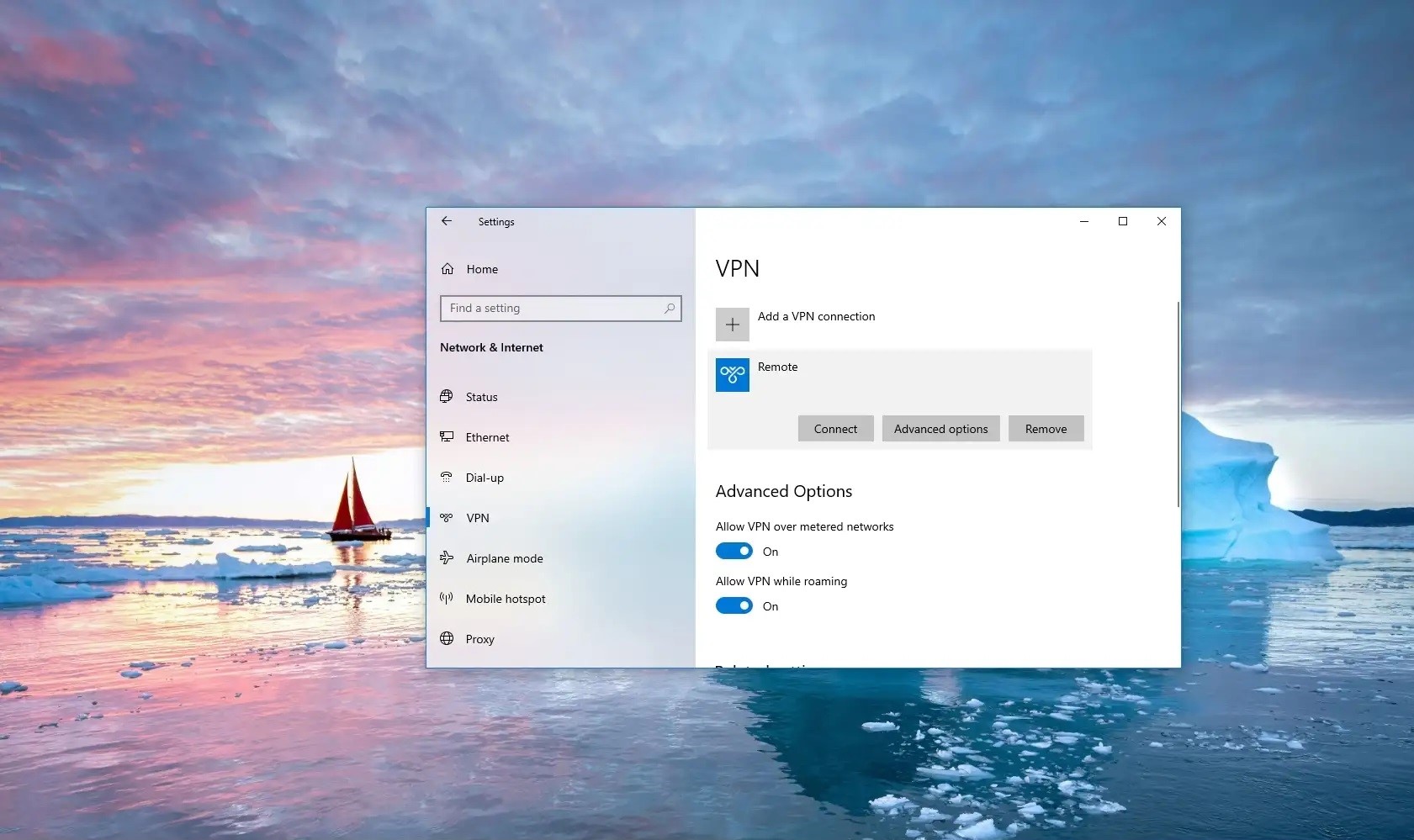
Configuring Advanced VPN Settings
After creating the basic VPN profile, you might need to configure additional settings:
- Advanced Options: From the VPN settings page, select the VPN connection you want to edit and then select Advanced options.
- Edit: Click on Edit next to the details you want to update.
- Proxy Settings: If necessary, specify proxy settings for your VPN connection.
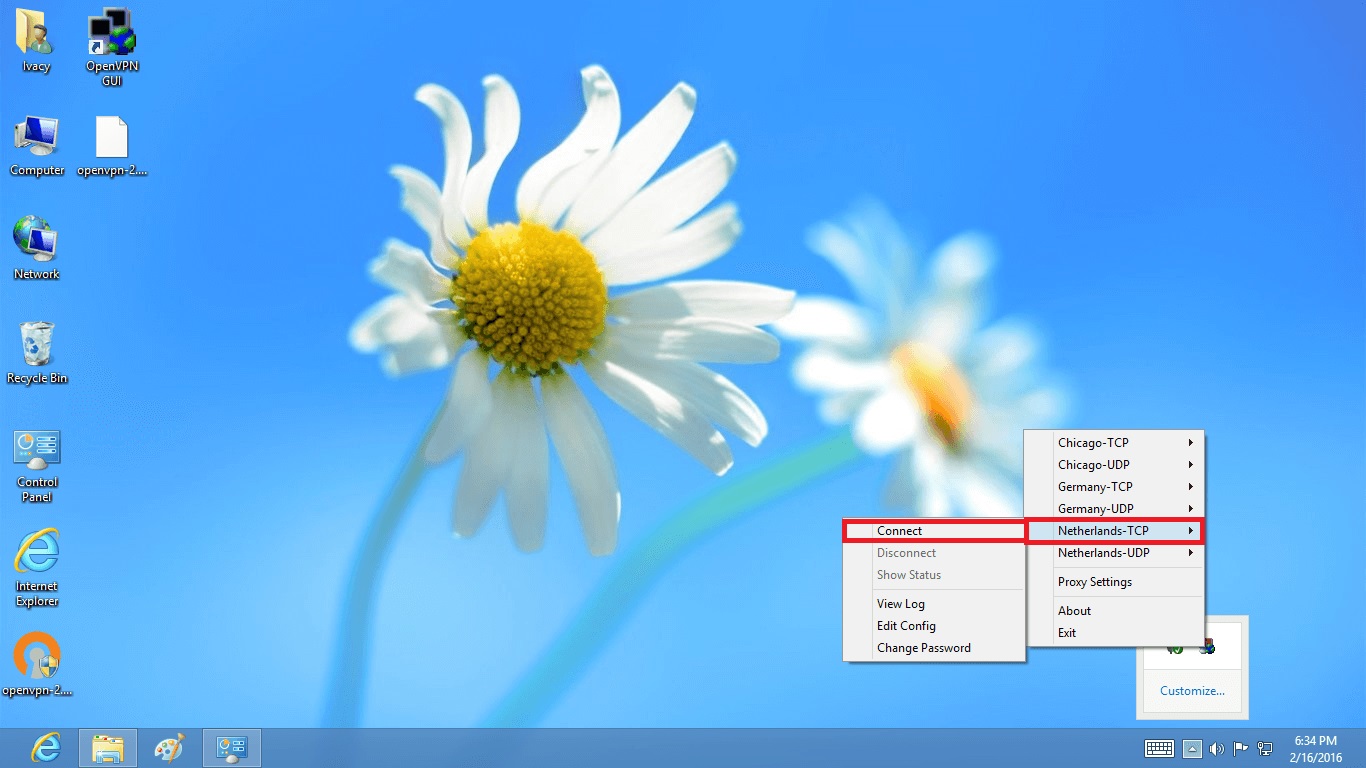
Connecting to a VPN
Once you have set up your VPN profile, connecting to it is straightforward:
- Open Settings: Click on the Start button and select Settings.
- Network & Internet: Navigate to Network & Internet.
- VPN: Click on VPN.
- Your VPN Connection: Find your created VPN connection and click on Connect.
Read more: Mastering VPN on Mac: A Comprehensive Guide
Managing VPN Connections
Windows provides several tools to manage your VPN connections:
- VPN Status: Check the status of your VPN connection by going to Network & Internet > VPN.
- Disconnect: To disconnect from a VPN, simply click on Disconnect next to your active VPN connection.
- Delete VPN Profile: If you no longer need a VPN profile, delete it by selecting the profile and clicking on Delete.
Troubleshooting VPN Issues
Sometimes, VPN connections can be problematic. Here are some common issues and their solutions:
Connection Issues
- Check Server Status: Ensure that the VPN server is up and running.
- Check Internet Connection: Make sure your internet connection is stable.
- Check VPN Settings: Double-check your VPN settings for any errors or typos.
Authentication Issues
- Check Credentials: Verify that your username and password are correct.
- Check Certificate: If using a certificate, ensure it is valid and correctly configured.
Read more: Exploring the Ports of Chromecast
Encryption Issues
- Check VPN Type: Ensure that the chosen VPN type supports encryption (e.g., IKEv2, OpenVPN).
- Check Firewall Settings: Sometimes, firewalls can block VPN traffic. Check your firewall settings to ensure they are not blocking the VPN connection.
Advanced VPN Configuration
For more advanced users, several additional configurations can be made:
Using Third-Party VPN Software
While Windows provides built-in support for VPNs, third-party software can offer more features and better performance. Some popular third-party VPN clients include ExpressVPN, NordVPN, and TunnelBear.
Configuring Split Tunneling
Split tunneling allows you to choose which applications use the VPN and which do not. This can be useful for balancing security with performance.
- Open VPN Settings: Go to Network & Internet > VPN.
- Edit VPN Connection: Select the VPN connection you want to edit.
- Advanced Options: Click on Advanced options.
- Split Tunneling: Enable split tunneling and specify which applications should use the VPN.
Configuring DNS Leak Protection
DNS leak protection ensures that your DNS queries are routed through the VPN server, preventing leaks of your real IP address.
- Open VPN Settings: Go to Network & Internet > VPN.
- Edit VPN Connection: Select the VPN connection you want to edit.
- Advanced Options: Click on Advanced options.
- DNS Leak Protection: Enable DNS leak protection if available.
Securing Your VPN Connection
Securing your VPN connection is crucial to prevent unauthorized access to your data:
Using Strong Passwords
Use strong, unique passwords for your VPN account.
Enabling Two-Factor Authentication (2FA)
Enable 2FA whenever possible to add an extra layer of security.
Read more: Using VPN on Smart TV: A Comprehensive Guide
Regularly Updating Your VPN Software
Regularly update your VPN software to ensure you have the latest security patches.
Final Thoughts
Setting up and managing a VPN on Windows is a straightforward process that can significantly enhance your online security. By following the steps outlined in this guide, you can create and configure a VPN connection that meets your needs. Troubleshoot common issues and secure your connection to ensure maximum protection. Whether you're a personal user or an enterprise administrator, understanding how to work with VPNs on Windows is essential for maintaining a secure digital environment.