Home>Software and Apps>Lost Phone? Use Google Authenticator


Software and Apps
Lost Phone? Use Google Authenticator
Modified: September 5, 2024
Protect your data with Google Authenticator. Safeguard your software and apps with this essential tool. Don't let a lost phone compromise your security.
(Many of the links in this article redirect to a specific reviewed product. Your purchase of these products through affiliate links helps to generate commission for Techsplurge.com, at no extra cost. Learn more)
Table of Contents
Introduction
Losing a phone can be a daunting experience, especially when it comes to managing online security. Two-factor authentication (2FA) adds an extra layer of protection to accounts. Google Authenticator is a popular 2FA app that generates time-based one-time passwords (TOTPs). If you lose your phone, recovering access to accounts might seem challenging. This guide will walk you through using Google Authenticator, setting it up, transferring it to a new device, and steps to take if your phone is lost.
Setting Up Google Authenticator
Download and Install Google Authenticator
- Open Google Play Store on Android or App Store on iOS.
- Search for "Google Authenticator" and download the app.
- Install and open the app.
Add Accounts
- Tap the "+" icon at the bottom right corner.
- Select "Add account."
- Choose the type of account (e.g., Google, Microsoft).
- Follow prompts to scan a QR code or enter a secret key provided by the service.
Verify Setup
- After adding an account, a six-digit code appears on the screen.
- Enter this code on the website or app to verify Google Authenticator is working correctly.
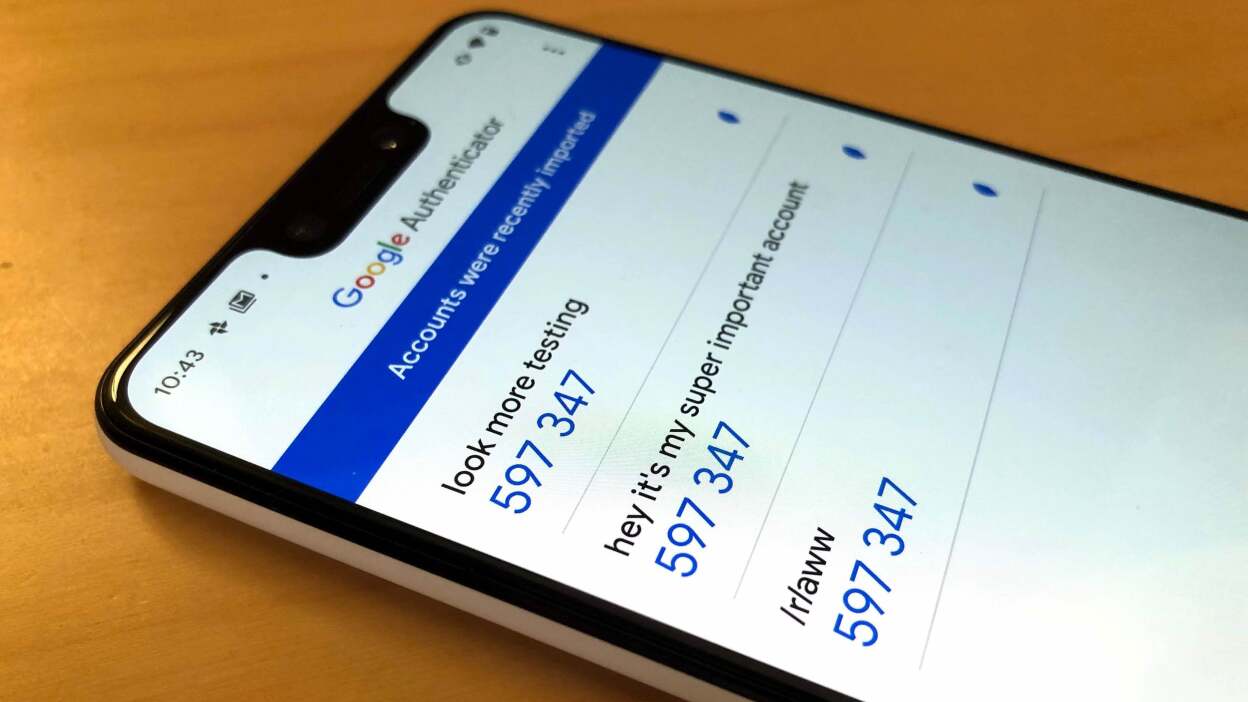
Transferring Google Authenticator to a New Device
QR Code Method
- On the new device, open Google Authenticator and tap the "+" icon.
- Select "Add account" and choose "Scan a QR code."
- Use the old device to scan the QR code displayed on the new device. This transfers all accounts from the old device to the new one.
Secret Key Method
- If scanning a QR code isn't possible, use the secret key provided by each service.
- Go to the settings of each service (e.g., Google Account settings) and find the "2-Step Verification" section.
- Under "Authenticator app," find the secret key. Write it down or save it securely.
- On the new device, open Google Authenticator and tap the "+" icon.
- Select "Add account" and choose "Enter a setup key."
- Enter the secret key saved earlier.
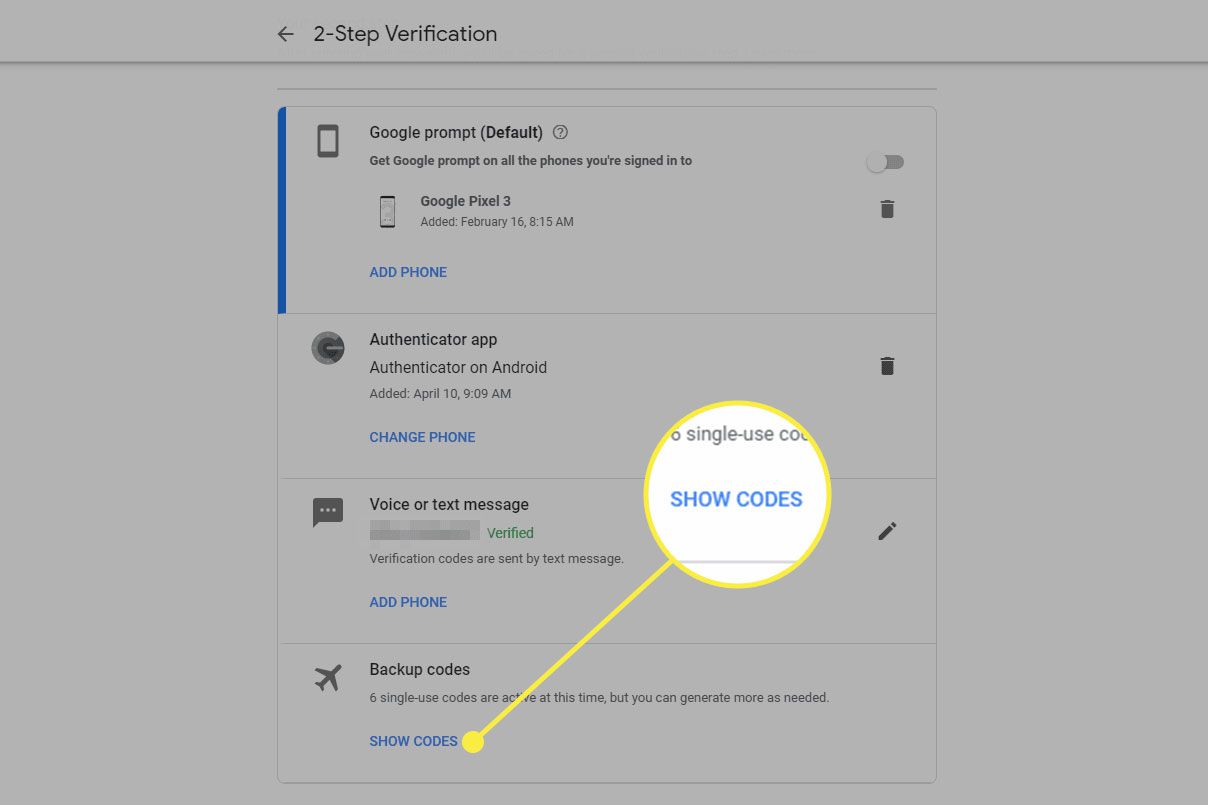
Backup Codes
- Some services provide backup codes for use if access to the authenticator app is lost.
- These codes are usually generated during 2FA setup and can be found in account settings.
- Write down these codes and store them securely. Consider saving them in a password manager or encrypted file.
Read more: Using Google Authenticator for Twitter
What to Do If You Lose Your Phone
Use Backup Codes
- If backup codes were generated by the service, use them to log into the account.
- Enter the backup code when prompted during the login process.
Contact Support
- If backup codes are unavailable, contact the support team of the service.
- They might help reset 2FA or provide additional assistance.
Use Alternative Authentication Methods
- Some services allow alternative authentication methods like SMS or email-based codes.
- Check account settings to see if this option is available.
Read more: How To Use Google Authenticator On PC
Set Up New Device Immediately
- If possible, set up Google Authenticator on a new device as soon as possible.
- This ensures not being locked out of accounts for an extended period.
Best Practices for Managing Google Authenticator
Regularly Back Up Accounts
- Use backup codes provided by each service and store them securely.
- Save these codes in a password manager or encrypted file.
Use Multiple Devices
- Install Google Authenticator on multiple devices (e.g., phone, tablet, laptop).
- This way, even if one device is lost, accounts can still be accessed using another.
Keep Devices Updated
- Ensure all devices are running the latest software updates.
- This helps prevent security vulnerabilities that could compromise accounts.
Store Physical Copies Securely
- Write down backup codes and store them in a secure location.
- Consider keeping a physical copy of these codes in a safe or secure location.
Educate Yourself on 2FA Options
- Understand different types of 2FA methods available (e.g., SMS, email-based codes, authenticator apps).
- Be prepared to switch between methods if needed.
Additional Tips
- Use a Password Manager: Consider using a password manager like LastPass or 1Password to store all login credentials and backup codes securely.
- Keep Secret Keys Safe: Write down secret keys and store them securely. Avoid sharing these keys with anyone.
- Regularly Review Accounts: Periodically review accounts linked to Google Authenticator to ensure no important information is missing.
By following these tips and understanding how to set up, transfer, and manage Google Authenticator, you'll be well-prepared to handle any situation related to online security.