Home>Software and Apps>Google Authenticator Key: Enhancing Security With Two-Factor Authentication

Software and Apps
Google Authenticator Key: Enhancing Security With Two-Factor Authentication
Modified: May 29, 2024
Enhance the security of your software and apps with Google Authenticator key, a two-factor authentication solution that adds an extra layer of protection to your accounts. Strengthen your digital defenses and keep your sensitive information safe.
(Many of the links in this article redirect to a specific reviewed product. Your purchase of these products through affiliate links helps to generate commission for Techsplurge.com, at no extra cost. Learn more)
Table of Contents
Introduction
In today's digital age, security is paramount. With cyber threats on the rise, it's crucial to fortify our online accounts with robust protection. One of the most effective methods for enhancing security is through the implementation of two-factor authentication (2FA). This additional layer of security goes beyond the traditional password, providing an extra barrier against unauthorized access.
Two-factor authentication works by requiring two forms of verification before granting access to an account. Typically, this involves something the user knows, such as a password, combined with something they have, like a unique code. This approach significantly reduces the risk of unauthorized access, as even if a password is compromised, the second factor acts as a safeguard.
Among the various methods of 2FA, the Google Authenticator Key stands out as a popular and reliable choice. It offers a seamless and secure way to generate time-based one-time passwords (TOTPs) for authentication. By leveraging this technology, users can bolster the security of their accounts across a wide range of platforms, including email, social media, and financial services.
In the following sections, we will delve into the intricacies of two-factor authentication, explore the myriad benefits of using the Google Authenticator Key, and provide a comprehensive guide on setting up and utilizing this powerful security tool. Additionally, we will address common issues and offer valuable tips to ensure a smooth and secure experience with the Google Authenticator Key.
As we navigate through the realm of digital security, it's essential to equip ourselves with the knowledge and tools necessary to safeguard our online presence. By understanding the significance of two-factor authentication and harnessing the capabilities of the Google Authenticator Key, we can fortify our defenses and mitigate the risks associated with cyber threats. Let's embark on this journey to bolster our digital security and embrace the peace of mind that comes with knowing our accounts are well-protected.
Read more: The Secret Key for Google Authenticator
Understanding Two-Factor Authentication
Two-factor authentication (2FA) is a pivotal security measure designed to fortify the protection of online accounts. It adds an extra layer of defense beyond the conventional password, thereby significantly reducing the risk of unauthorized access. The fundamental principle of 2FA revolves around the requirement for two distinct forms of verification before granting access to an account. This typically involves something the user knows, such as a password, combined with something they have, like a unique code or physical device.
The primary goal of 2FA is to mitigate the vulnerabilities associated with relying solely on passwords for account security. Passwords, despite being a ubiquitous form of authentication, are susceptible to various threats, including phishing attacks, brute force attempts, and password leaks. By introducing an additional factor, 2FA addresses these vulnerabilities and enhances the overall security posture of online accounts.
The two factors in 2FA can be categorized into three main types: knowledge factors, possession factors, and inherence factors. Knowledge factors encompass information that the user knows, such as a password or a personal identification number (PIN). Possession factors involve something that the user possesses, such as a mobile device, security token, or smart card. Inherence factors are based on the user's unique biological traits, such as fingerprint or iris scans.
One of the most prevalent implementations of 2FA involves the use of one-time passwords (OTPs), which are temporary codes that expire after a short duration. These time-based OTPs add an element of dynamism to the authentication process, rendering them useless for malicious actors after a brief period. This time-sensitive nature enhances the security of the authentication process, as the codes cannot be reused or intercepted for unauthorized access.
By requiring two distinct forms of verification, 2FA significantly raises the bar for potential attackers, making it more challenging for them to compromise accounts. Even if a password is compromised through a data breach or social engineering attack, the additional factor acts as a robust safeguard, thwarting unauthorized access attempts.
In essence, understanding two-factor authentication is pivotal in recognizing its role as a potent defense mechanism against a myriad of cyber threats. By embracing the principles of 2FA and integrating it into our digital security practices, we can bolster the resilience of our online accounts and mitigate the risks associated with unauthorized access.
Benefits of Using Google Authenticator Key
The Google Authenticator Key offers a multitude of benefits that elevate the security of online accounts and streamline the authentication process. By leveraging this robust tool, users can fortify their digital defenses while enjoying a seamless and efficient authentication experience.
-
Enhanced Security: The foremost benefit of using the Google Authenticator Key is the bolstering of security for online accounts. By implementing time-based one-time passwords (TOTPs), the Authenticator Key adds an extra layer of defense, making it significantly more challenging for unauthorized individuals to gain access. This heightened security is particularly crucial in safeguarding sensitive information, financial assets, and personal data from potential threats.
-
Protection Against Phishing: The Google Authenticator Key mitigates the risks associated with phishing attacks, which often aim to deceive users into divulging their login credentials. Unlike traditional SMS-based authentication methods, TOTPs generated by the Authenticator Key are not susceptible to interception or redirection by malicious actors, thereby thwarting phishing attempts and enhancing account security.
-
Offline Access: Unlike some other 2FA methods that rely on internet connectivity, the Google Authenticator Key operates offline, allowing users to generate TOTPs even in situations where network access is limited. This offline functionality ensures that users can securely authenticate their accounts regardless of their location or connectivity status, adding a layer of convenience without compromising security.
-
Versatility and Compatibility: The Google Authenticator Key is compatible with a wide array of online platforms and services, including email providers, social media networks, cryptocurrency exchanges, and more. Its versatility enables users to consolidate their 2FA requirements within a single, user-friendly application, streamlining the authentication process across various accounts.
-
User-Friendly Interface: The Authenticator Key offers a user-friendly interface that simplifies the process of generating and inputting TOTPs. With its intuitive design and straightforward functionality, users can seamlessly navigate the application, making the authentication process efficient and accessible for individuals of varying technical proficiencies.
-
Multi-Device Synchronization: The Google Authenticator Key supports multi-device synchronization, allowing users to securely transfer their 2FA configurations to new devices. This feature enhances flexibility and convenience, enabling users to seamlessly transition to new hardware without the hassle of reconfiguring their authentication settings.
In essence, the Google Authenticator Key stands as a formidable ally in the realm of digital security, offering a host of benefits that fortify the protection of online accounts while ensuring a user-friendly and versatile authentication experience. By harnessing the capabilities of the Authenticator Key, individuals can elevate their security posture and navigate the digital landscape with confidence and peace of mind.
Setting Up Google Authenticator Key
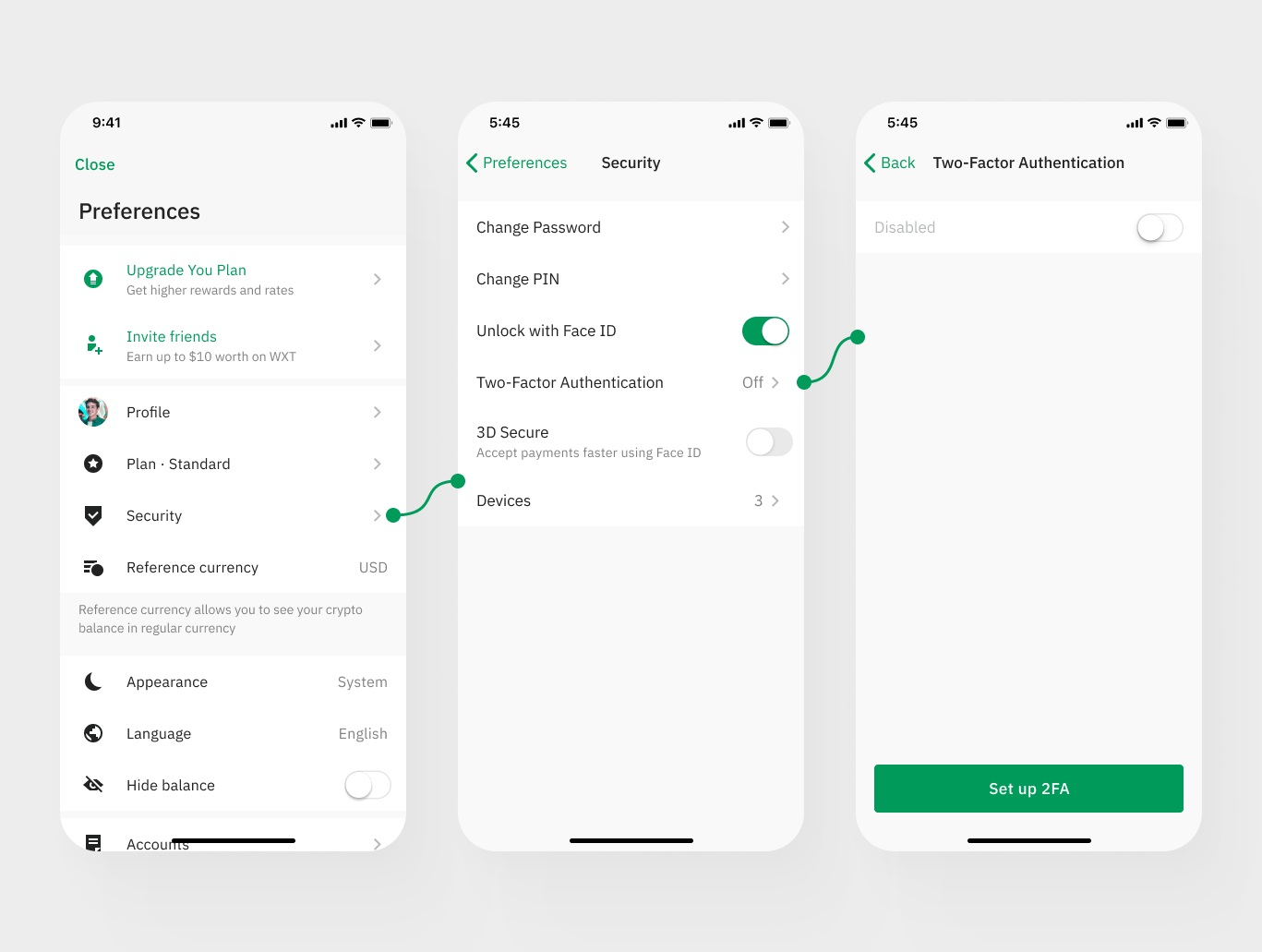
Setting up the Google Authenticator Key is a straightforward process that empowers users to fortify the security of their online accounts. To begin, users can download the Google Authenticator app from the Google Play Store for Android devices or the App Store for iOS devices. Once the app is installed, the setup process involves a few simple steps to enable the generation of time-based one-time passwords (TOTPs) for 2FA.
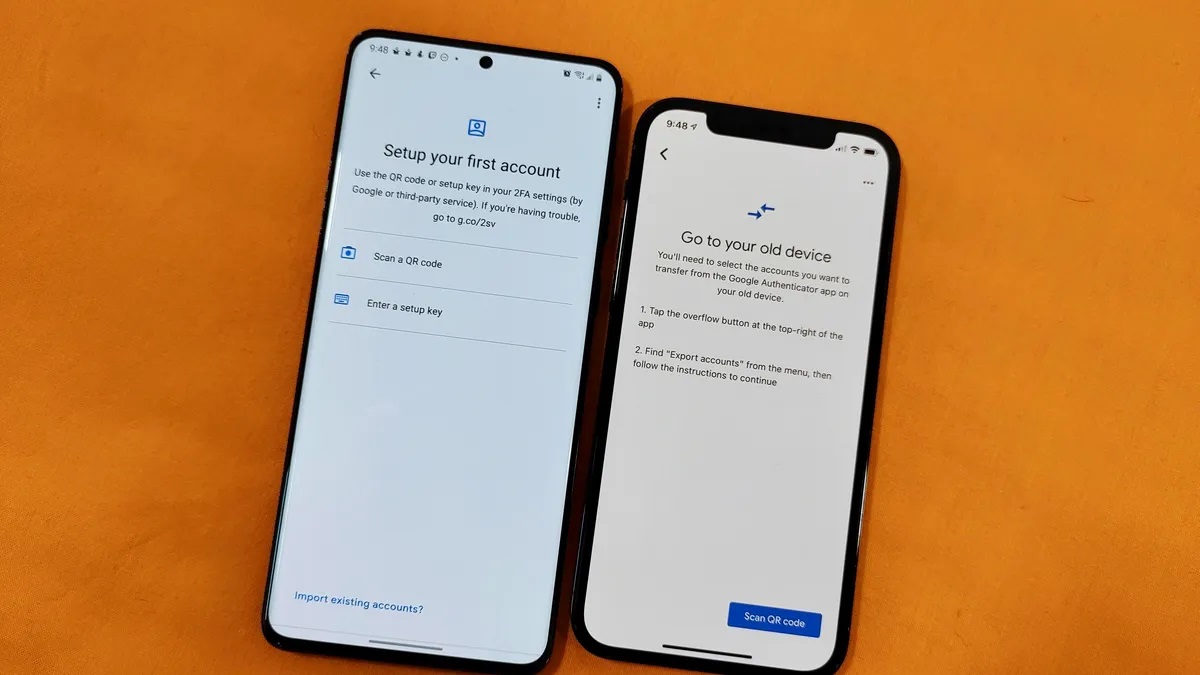
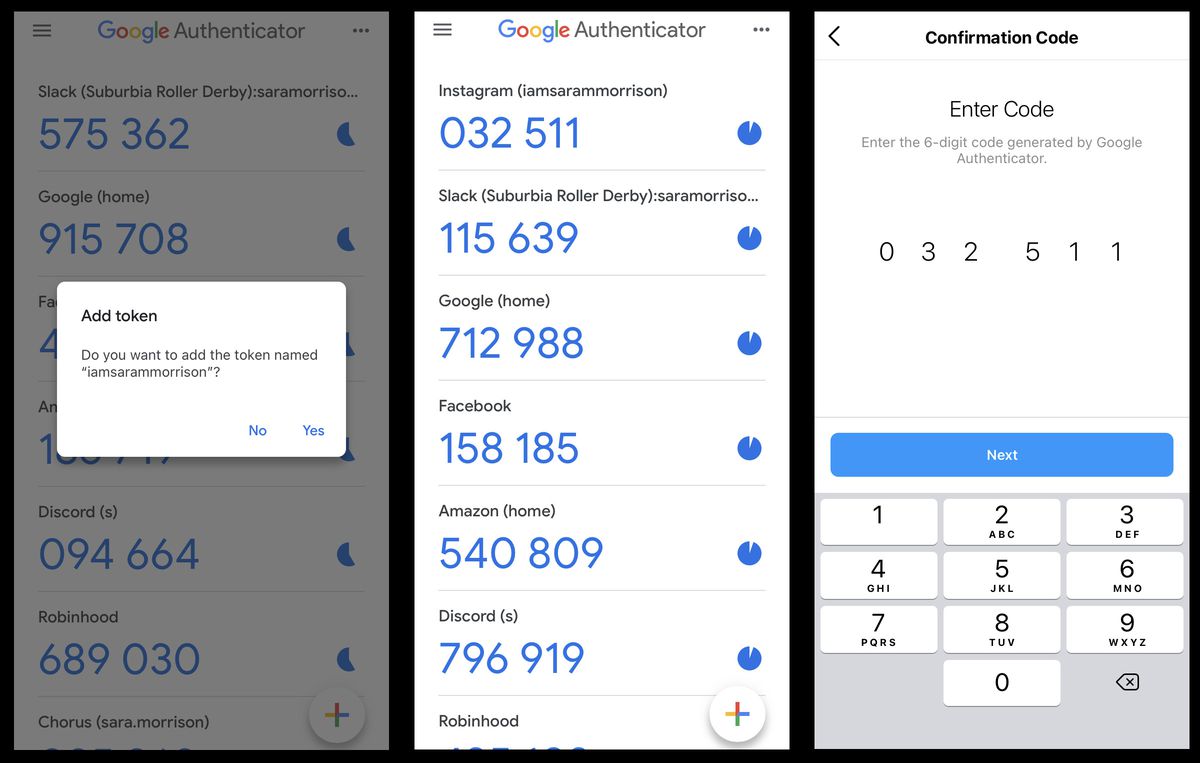
Upon launching the Google Authenticator app, users can initiate the setup by selecting the option to add a new account. This prompts the app to present a barcode or a manual entry option. For platforms that support QR code scanning, users can simply scan the provided barcode using the app. Alternatively, they can opt for the manual entry method by entering the account name and the secret key provided by the respective service or platform.
After adding the account, the Google Authenticator app will begin generating TOTPs for the configured account. Each code is time-based and refreshes at regular intervals, ensuring that the authentication process remains dynamic and secure. Users can then proceed to input the generated TOTP when prompted during the login process for the associated account.
It's important to note that the Google Authenticator Key can be set up for multiple accounts, offering a centralized and streamlined approach to managing 2FA across various platforms. This consolidation of authentication requirements within a single application enhances convenience and security, as users can efficiently navigate their 2FA configurations without the need for multiple authentication methods.
Furthermore, the Google Authenticator app supports multi-device synchronization, allowing users to securely transfer their 2FA configurations to new devices. This feature adds a layer of flexibility, enabling seamless transitions to new hardware without the hassle of reconfiguring authentication settings.
By following these simple steps and leveraging the capabilities of the Google Authenticator app, users can establish a robust and user-friendly 2FA solution that enhances the security of their online accounts. The setup process is designed to be intuitive and accessible, empowering individuals to fortify their digital defenses with ease and confidence.
Using Google Authenticator Key for Different Accounts
The versatility of the Google Authenticator Key extends to its seamless integration with a diverse range of online accounts and services. Leveraging this robust 2FA solution across different platforms empowers users to fortify the security of their accounts while enjoying a streamlined authentication experience.
Read more: How To Turn Off Two Factor Authentication
Email Accounts
The Google Authenticator Key can be utilized to enhance the security of email accounts across various providers, including Gmail, Outlook, Yahoo Mail, and more. By configuring the Authenticator Key for email authentication, users can safeguard their communication channels and sensitive information from unauthorized access.
Social Media Platforms
Popular social media networks such as Facebook, Twitter, Instagram, and LinkedIn offer support for 2FA, allowing users to bolster the security of their accounts with the Google Authenticator Key. This additional layer of defense mitigates the risks associated with unauthorized access and safeguards personal and professional profiles from potential threats.
Financial Services
Banking institutions, investment platforms, and cryptocurrency exchanges increasingly prioritize security, making 2FA an essential component of account protection. By integrating the Google Authenticator Key with financial services, users can fortify the defense of their assets and sensitive financial information, mitigating the risks associated with unauthorized transactions and account breaches.
Cloud Storage and Productivity Tools
Leading cloud storage providers and productivity platforms, such as Google Drive, Dropbox, Microsoft OneDrive, and productivity suites like Microsoft 365 and Google Workspace, offer support for 2FA. By leveraging the Google Authenticator Key, users can bolster the security of their cloud-based data and collaborative tools, ensuring the integrity and confidentiality of their digital assets.
Read more: Is Google Authenticator Secure?
E-commerce and Online Retail
With the prevalence of online shopping and e-commerce transactions, securing accounts on platforms like Amazon, eBay, and Shopify is paramount. The Google Authenticator Key provides an additional layer of defense, safeguarding personal and financial information from unauthorized access and potential fraudulent activities.
Gaming and Entertainment Platforms
Gaming accounts and entertainment services, including popular platforms like Steam, PlayStation Network, and Netflix, can benefit from the enhanced security offered by the Google Authenticator Key. By implementing 2FA, users can protect their gaming progress, digital content, and entertainment subscriptions from unauthorized access and potential account compromise.
In essence, the Google Authenticator Key serves as a versatile and robust 2FA solution that seamlessly integrates with a myriad of online accounts and services. By leveraging this powerful tool across different platforms, users can fortify the security of their digital presence, mitigate the risks associated with unauthorized access, and navigate the digital landscape with confidence and peace of mind.
Troubleshooting and Tips for Google Authenticator Key
As users embrace the Google Authenticator Key to fortify the security of their online accounts, it's essential to be equipped with troubleshooting insights and valuable tips to ensure a seamless and secure experience. Here are some key considerations to address common issues and optimize the utilization of the Authenticator Key:
Time Synchronization:
One common issue that users may encounter is time synchronization discrepancies between the device running the Google Authenticator app and the server hosting the 2FA-protected service. This misalignment can lead to authentication failures. To mitigate this, ensure that the device's system time is accurately synchronized with a reliable time source, such as network time protocol (NTP) servers.
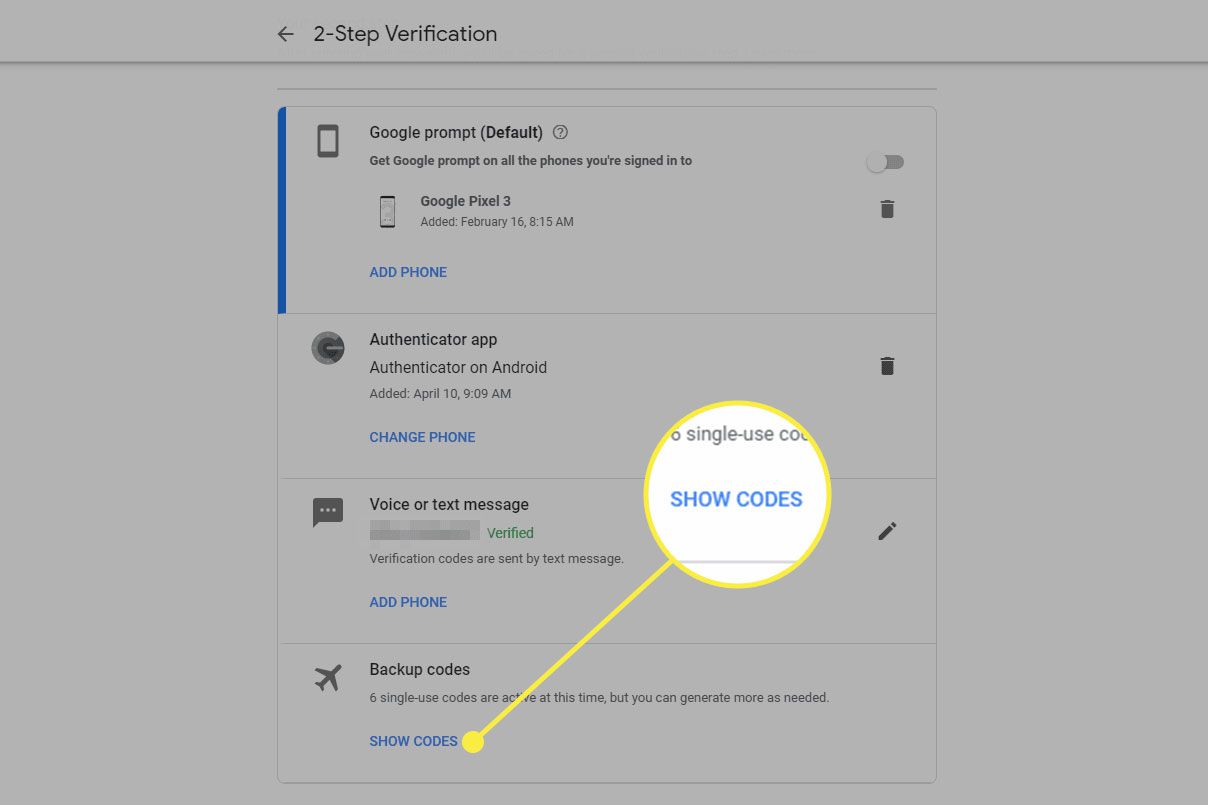
Backup and Recovery Codes:
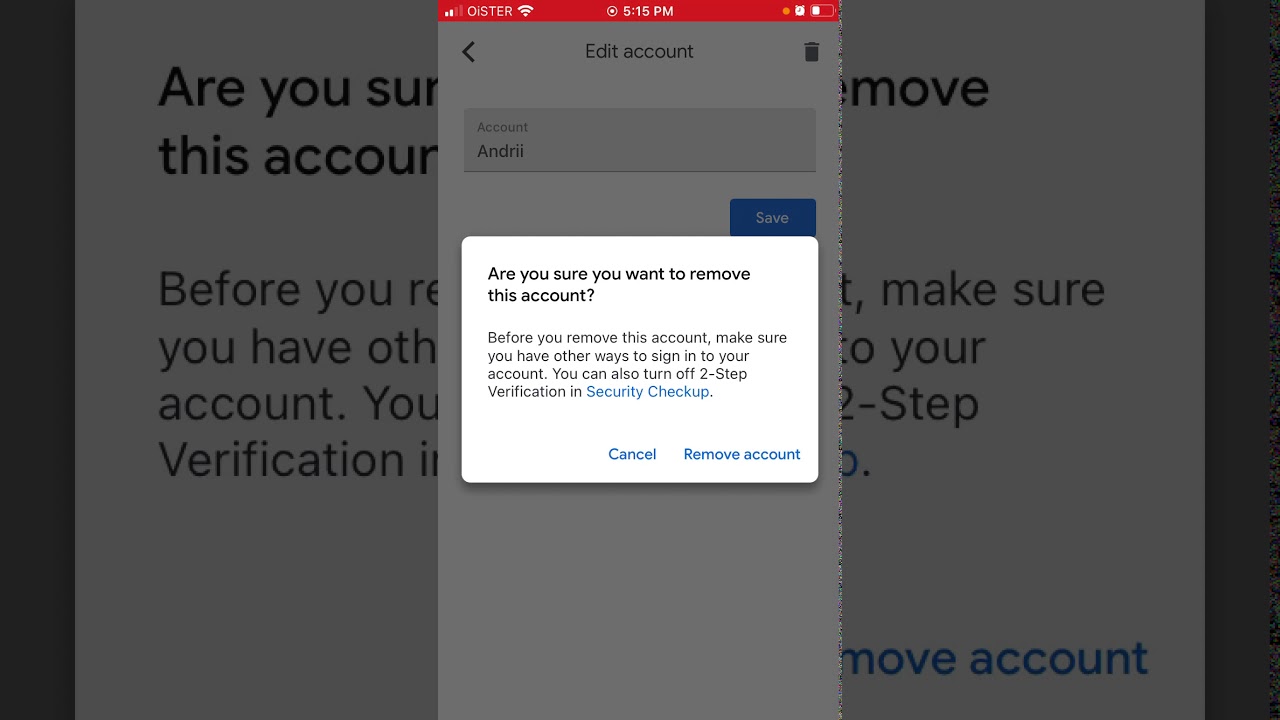
In the event of device loss or failure, having backup and recovery codes is crucial. Many platforms that support the Google Authenticator Key provide users with backup codes during the initial setup. It's imperative to securely store these codes in a separate, accessible location to facilitate account recovery if the primary device is unavailable.
Multiple Device Setup:
For users who rely on multiple devices, setting up the Google Authenticator Key across all devices is advisable. This ensures accessibility and redundancy, allowing seamless authentication even if one device becomes inaccessible. Leveraging the multi-device synchronization feature of the Authenticator app facilitates this setup.
Account Recovery Procedures:
Familiarize yourself with the account recovery procedures offered by the platforms where the Google Authenticator Key is employed. Understanding the steps for account recovery, including alternative authentication methods or support channels, can mitigate potential challenges in regaining access to your accounts.
Secure Device Management:
Maintain a proactive approach to device security, as the Google Authenticator Key's effectiveness is contingent on the security of the device where it is installed. Implementing strong device passcodes, enabling biometric authentication where available, and regularly updating device software contribute to a secure environment for 2FA operations.
Read more: The Power of Google Authenticator
Periodic Review and Cleanup:
Regularly review the accounts linked to the Google Authenticator Key to ensure that the configured services are still relevant and actively used. Removing unused or obsolete accounts from the Authenticator app streamlines the authentication process and reduces clutter, enhancing overall efficiency.
By adhering to these troubleshooting insights and implementing the recommended tips, users can optimize their experience with the Google Authenticator Key, mitigate potential challenges, and fortify the security of their online accounts. Embracing a proactive and informed approach to 2FA utilization empowers individuals to navigate the digital landscape with confidence and resilience.