Home>Software and Apps>The Secret Key for Google Authenticator

Software and Apps
The Secret Key for Google Authenticator
Modified: September 5, 2024
Discover the best software and apps for setting up and using Google Authenticator to enhance your online security. Learn the secret key and more.
(Many of the links in this article redirect to a specific reviewed product. Your purchase of these products through affiliate links helps to generate commission for Techsplurge.com, at no extra cost. Learn more)
Table of Contents
The Secret Key for Google Authenticator: A Comprehensive Guide
Google Authenticator is a popular two-factor authentication (2FA) app that adds an extra layer of security to online accounts. It generates time-based one-time passwords (TOTPs) synchronized across devices, ensuring only authorized users can access accounts. However, the secret key, a core component of Google Authenticator, often remains a mystery. This guide will explain what secret keys are, how they work, and how to manage them effectively.
What is a Secret Key?
A secret key in Google Authenticator is a unique string of characters used to generate TOTP codes. Typically, this key is a 16-character alphanumeric code generated during setup. The secret key is essential for synchronizing TOTP codes across devices, ensuring consistent access to accounts.
How Does the Secret Key Work?
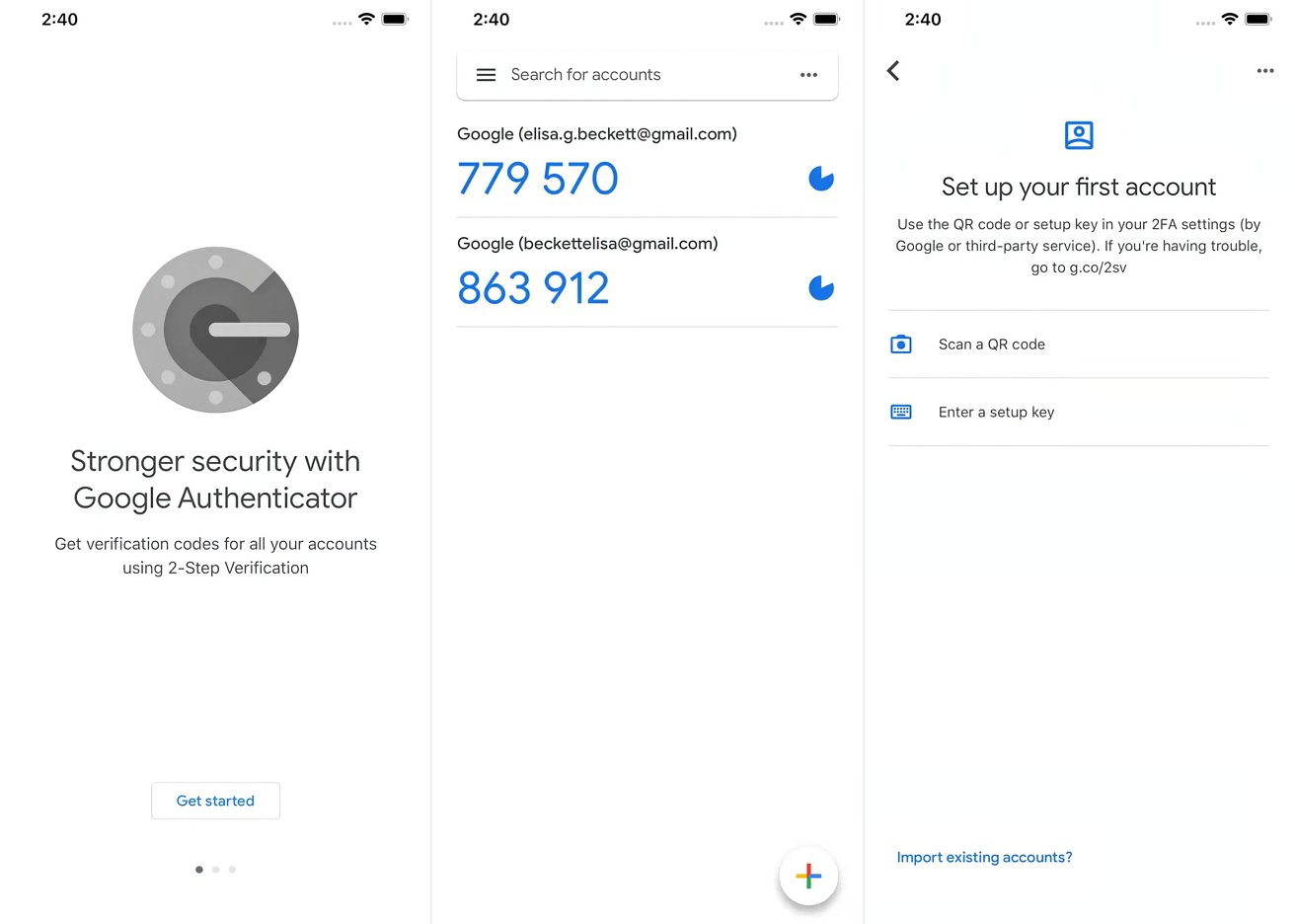
During Google Authenticator setup, users can either scan a QR code or enter the secret key manually. Scanning the QR code automatically generates and stores the secret key locally. Manually entering the secret key requires copying and pasting the provided code into the app.
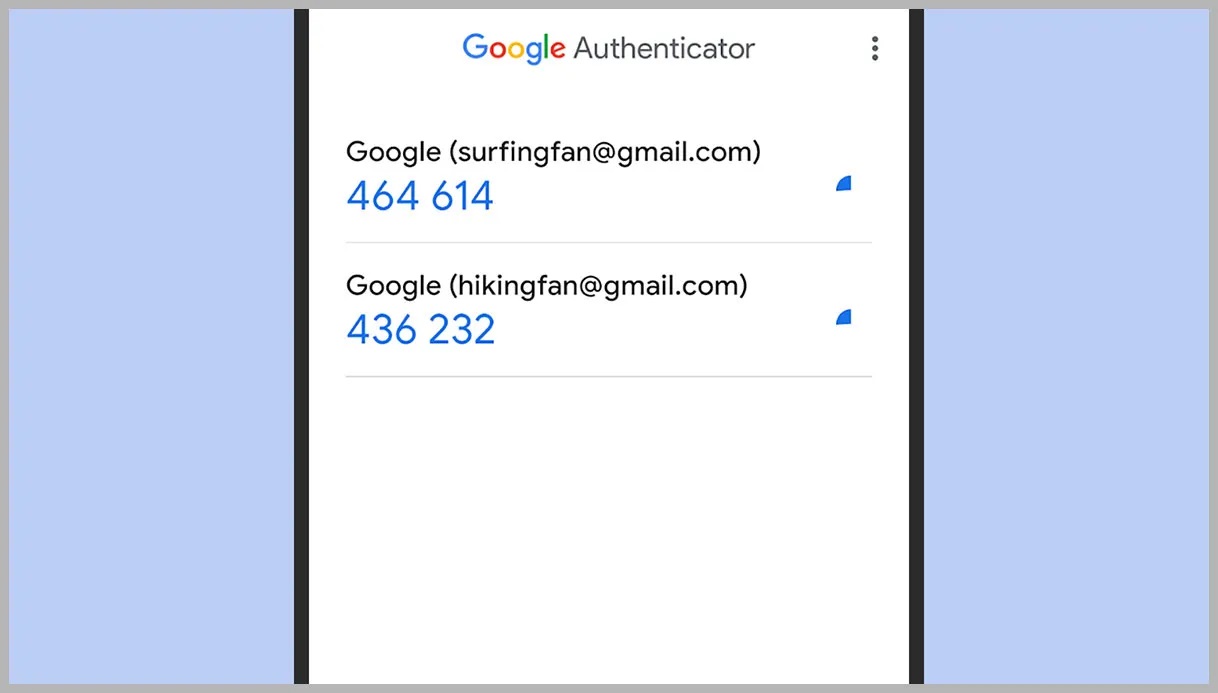
Once stored, Google Authenticator uses the secret key to generate TOTP codes at regular intervals, usually every 30 seconds. These codes are based on the current time and the secret key, ensuring frequent changes and unique codes for each time period.
Importance of the Secret Key
The secret key is crucial for several reasons:
- Security: Ensures only authorized users can access accounts. Unauthorized access to the secret key allows others to generate the same TOTP codes.
- Synchronization: Allows synchronization of TOTP codes across devices. With the same secret key on multiple devices, users receive identical TOTP codes, ensuring access from any device.
- Verification: Used to verify the authenticity of TOTP codes. When entering a TOTP code on a login page, the server checks the code against the secret key stored in its database. Matching codes grant account access.
Managing Your Secret Key
Effective management of the secret key is vital for maintaining account security. Here are some best practices:
Read more: How to Backup Google Authenticator
1. Store Your Secret Key Securely
- Do Not Share: Never share the secret key. Unauthorized access to the key allows others to generate the same TOTP codes.
- Use a Password Manager: Store the secret key securely using a password manager. These tools provide robust encryption and secure storage for sensitive information.
- Keep It Private: Avoid sharing the secret key with anyone, including family members or colleagues.
2. Use a Secure Method to Enter the Secret Key
- Use HTTPS: Always use HTTPS when entering the secret key manually. This ensures encrypted communication between the device and the server, reducing interception risks.
- Avoid Public Wi-Fi: Avoid entering the secret key on public Wi-Fi networks, as these are often unsecured and easily intercepted by hackers.
3. Regularly Update Your Devices
- Update Your Operating System: Regularly update the operating system to ensure the latest security patches.
- Update Google Authenticator: Regularly update Google Authenticator for the latest features and security patches.
4. Use Additional Security Measures
- Enable Privacy Screen: Enable the privacy screen in Google Authenticator to require a verification prompt before app use. This adds an extra layer of security by requiring a PIN, pattern, or biometric prompt.
- Use Two-Factor Authentication: Use two-factor authentication (2FA) whenever possible. This requires both a password and a TOTP code for account access.
How to Add a Secret Key Manually
If adding a secret key manually is necessary, follow these steps:
- Open the TypingDNA Chrome Extension: Click on “Add code manually.”
- Copy the Secret Code: Copy the secret code generated by the website.
- Paste the Secret Code: Paste the secret code into the TypingDNA Authenticator in the Secret (16-char code) field.
- Give Your Account a Title: Assign a memorable title to the account (e.g., Coinbase).
- Save the Account: Click the Save button to save the account.
Using Google Authenticator Without a Google Account
Google Authenticator can be used without a Google account. This is useful for saving codes safely in a Google Account while also having the option to use them without these protections. Follow these steps:
- Open Google Authenticator: Tap “Use without an account.”
- Remove Codes from Google Account: If codes are already saved to a Google Account, tap the profile picture at the top right corner of the home screen, then tap “Use Authenticator without an account.” This action removes codes from all Google Accounts and stores them on the device. Codes will not be available on other devices.
Organizing Your Google Authenticator Codes
Organizing Google Authenticator codes helps quickly find the needed code. Here are some tips:
- Touch and Hold: Touch and hold any code to reorder it.
- Use the Search Bar: Use the search bar to find the needed code. Enter any text matching the username to locate the code.
Deleting Your Google Authenticator Codes
Deleting Google Authenticator codes is important if they are no longer needed or if removal from all devices is required. Follow these steps:
- Swipe Right: Swipe right on any code to show the delete option.
- Confirm Deletion: Confirm deletion. If Authenticator codes are synced to a Google Account, they will also be deleted from all devices where codes are synced.
By understanding how the secret key works and following best practices for managing it, you can significantly improve the security of your online accounts. Store the secret key securely, use a secure method to enter it, regularly update devices, and use additional security measures to protect the secret key from being compromised. Following these guidelines ensures the full benefits of Google Authenticator while maintaining the highest level of security for your online presence.