Home>Software and Apps>Is Google Authenticator Secure?


Software and Apps
Is Google Authenticator Secure?
Modified: September 5, 2024
Learn about the security of Google Authenticator and how it keeps your software and apps safe. Find out if it's a reliable choice for your security needs.
(Many of the links in this article redirect to a specific reviewed product. Your purchase of these products through affiliate links helps to generate commission for Techsplurge.com, at no extra cost. Learn more)
Table of Contents
How Google Authenticator Works
Google Authenticator uses the Time-Based One-Time Password (TOTP) algorithm, specified in the Internet Engineering Task Force's (IETF) RFC 6238. This algorithm generates a six-digit OTP that changes every 30 seconds, making it highly secure and resistant to replay attacks. Here’s a step-by-step explanation of how Google Authenticator functions:
Installation
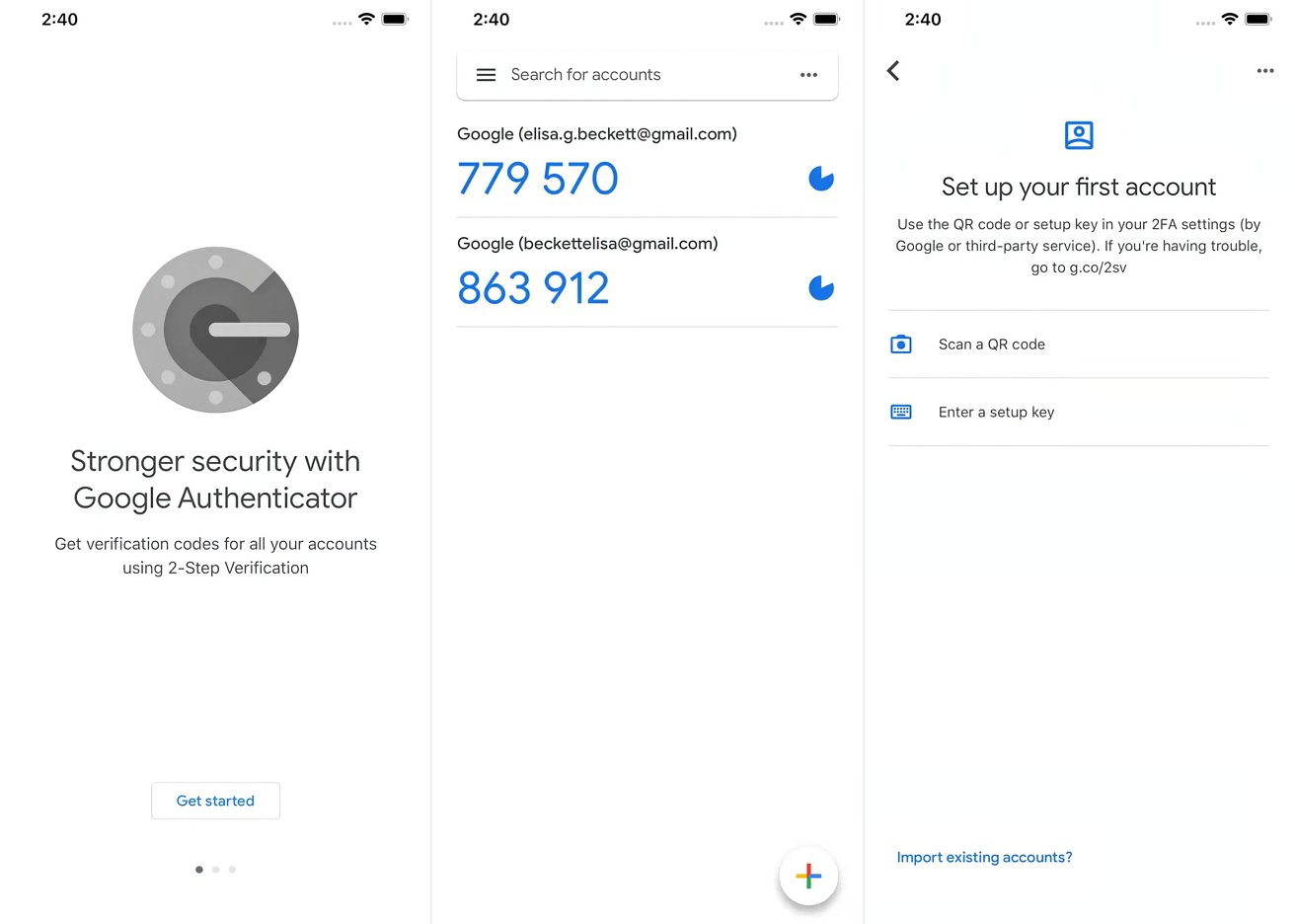
Users install the Google Authenticator app on their iOS or Android devices.
Setup
Enabling 2FA on the target site or service provides a QR code or setup key.
Configuration
Open Google Authenticator, tap the plus sign to add the target site or service, and either scan the QR code or enter the setup key.
Verification
The app generates the first OTP, which must be entered to complete the setup process.
Usage
Each time users log into the site or service, Google Authenticator generates a new OTP, which must be entered along with the username and password to verify identity.
Security Features of Google Authenticator
Google Authenticator offers several security features that make it a robust tool for 2FA:
Encryption
OTPs are encrypted both in transit and at rest, ensuring codes remain protected from potential bad actors.
Time-Based OTPs
The TOTP algorithm ensures each OTP is unique and changes every 30 seconds, making it difficult for hackers to intercept and reuse codes.
Read more: The Power of Google Authenticator
Device Possession
The authentication process assumes users possess the device on which Google Authenticator is installed, adding an additional layer of security against phishing attacks.
QR Code and Setup Key
QR codes and setup keys provide a convenient and secure way to configure the app without exposing sensitive information.
Vulnerabilities of Google Authenticator
Despite its robust security features, Google Authenticator is not immune to certain vulnerabilities and criticisms:
Phishing Resistance
One primary concern is its lack of phishing resistance. If users enter their OTP on a fake site, they may inadvertently provide their credentials to an attacker.
Read more: How to Backup Google Authenticator
Data Synchronization
Users must ensure OTPs are synchronized across all devices, which can be challenging if multiple devices are used or if the app is not properly configured.
Backup and Recovery
While Google Authenticator allows users to back up their codes, there is no built-in mechanism for recovering lost or compromised codes, which can lead to account lockouts.
Google Account Dependence
Users who store their OTPs in their Google Account may face issues if their account is compromised or banned, potentially leading to loss of access to all associated services.
Comparison with Other 2FA Methods
Google Authenticator is not the only 2FA method available, and each has its own set of advantages and disadvantages:
Read more: Resetting Google Authenticator
SMS-Based 2FA
SMS-based 2FA is less secure than Google Authenticator because text messages can be intercepted and spoofed. However, it is widely supported and easy to implement.
YubiKey
YubiKey is a hardware-based 2FA solution that provides additional security through physical possession and is resistant to phishing attacks. However, it requires a physical device and may not be as convenient as Google Authenticator.
Authy
Authy is another popular 2FA app that offers similar features to Google Authenticator but with additional security measures like password protection and backup options. However, it may not be as widely supported as Google Authenticator.
Best Practices for Using Google Authenticator
To maximize the security of Google Authenticator, users should follow these best practices:
Read more: Restoring Google Authenticator
Sync OTPs
Ensure OTPs are synchronized across all devices to avoid issues with code availability.
Use Backup
Regularly back up OTPs to prevent loss in case of device failure or compromise.
Monitor Accounts
Regularly monitor account activity to detect any suspicious behavior.
Avoid Phishing
Be cautious when entering OTPs, ensuring the site is legitimate and not a phishing attempt.
Read more: Google Authenticator: Is it Free?
Use Additional Security Measures
Consider using additional security measures like YubiKey or password protection for the 2FA vault.
Final Thoughts
Google Authenticator is a robust tool for 2FA, offering several security features that make it a reliable choice for many users. However, it is not without its vulnerabilities, particularly in terms of phishing resistance and data synchronization. By understanding these limitations and following best practices, users can maximize the security of Google Authenticator and ensure a safer online experience. While other 2FA methods like YubiKey and Authy offer additional security benefits, Google Authenticator remains a widely supported and effective solution for many users. Ultimately, the choice of 2FA method depends on individual needs and preferences, but with proper usage and awareness of its limitations, Google Authenticator can be a valuable component of a comprehensive security strategy.